
Wolf Infosec
THM-Warzone2

Hello everyone! This challenge on TryHackMe has a difficulty rating of "medium", I feel it was rated right where it needs to be. Depending upon your skillset and what you've worked on, you may find this challenge a bit easy or difficult.
You're currently working as a T1 Security Analyst for a MSSP. You've been assigned a case which there was an alert triggered for Misc activity, A Network Trojan Was Detected and Potential Corporate Privacy Violation.
Just a small bit of background, these alerts would have most likely an Intrusion Detection System (IDS) or an Intrusion Prevention System (IPS) however that would not be the case. You need to determine if the alerts received are a True Positive or a False Positive.
To do this challenge you'll want to spawn the Machine attached to the room as it will have the tools you'll need and the PCAP file needed for the analysis.
Once you've spawned the machine you'll see a directory on the desktop of your ubuntu machine labeled "Tools" as well as a Zone2.pcap file. If you go ahead and click on the "THM" logo in the top right corner of the spawned machine, you can start up WireShark by going into "All Applications" and scrolling until you see WireShark. Once it opens click on "File > Open" and browse to the pcap file on the desktop.
I personally just used WireShark to see if I could find anything suspicious on my own without using Brim or Network Miner, and well I did. I came across an IP address where there was a file downloaded that looked a bit suspect. If we right click on that particular packet (number 6) and choose Follow > HTTP stream it'll open a new window where we can follow each packet that is tied to this.
So let's jump into some of these questions. To find the answer to the first 2 Questions below I used BRIM - which I've never used this tool before and quite honestly I may have to put it into use at work! You can launch BRIM using terminal if you'd like or you can find it in the "All Applications". Once you start up BRIM you'll want to drag or open the pcap file that is on the machine desktop.
To get the first question in BRIM we will use the IP address we found in WireShark from packet 6, if you search that IP address you'll get some alerts that populate. To analyze these alerts you will want to double click on each one. This will open a pop out window that will give you some information on the packet.
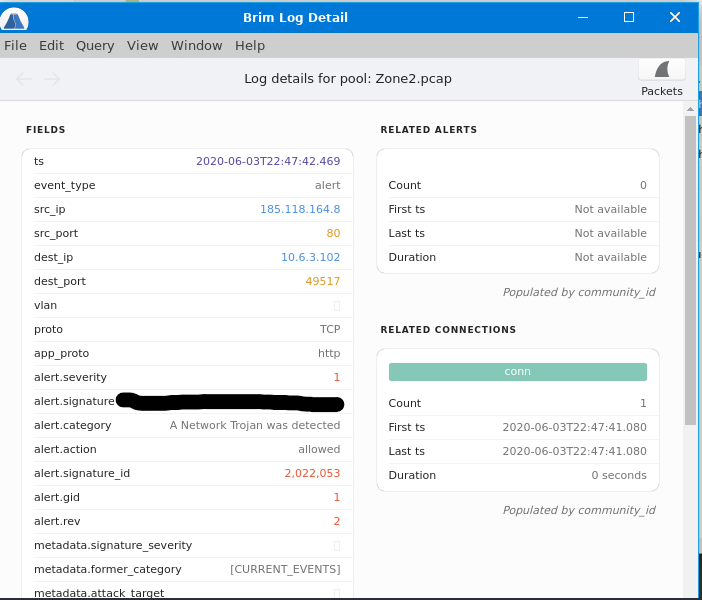
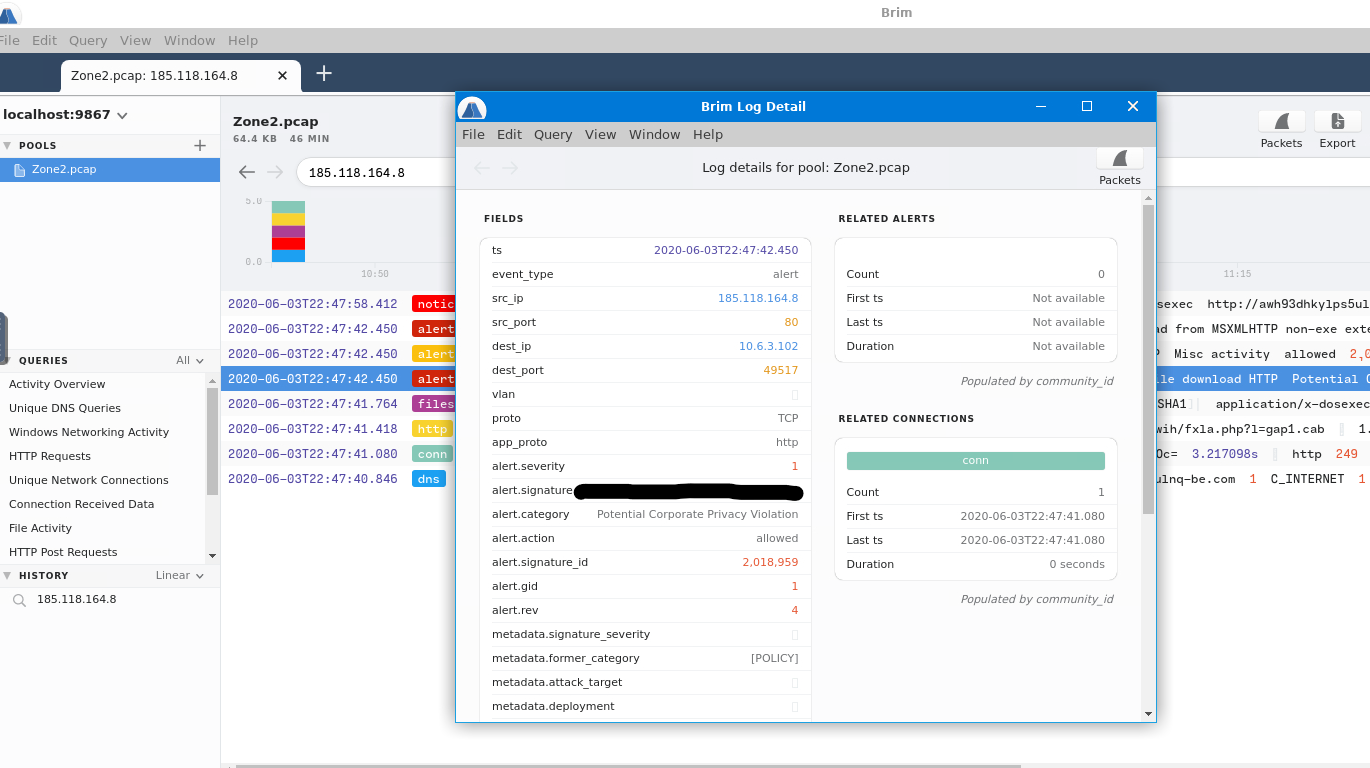
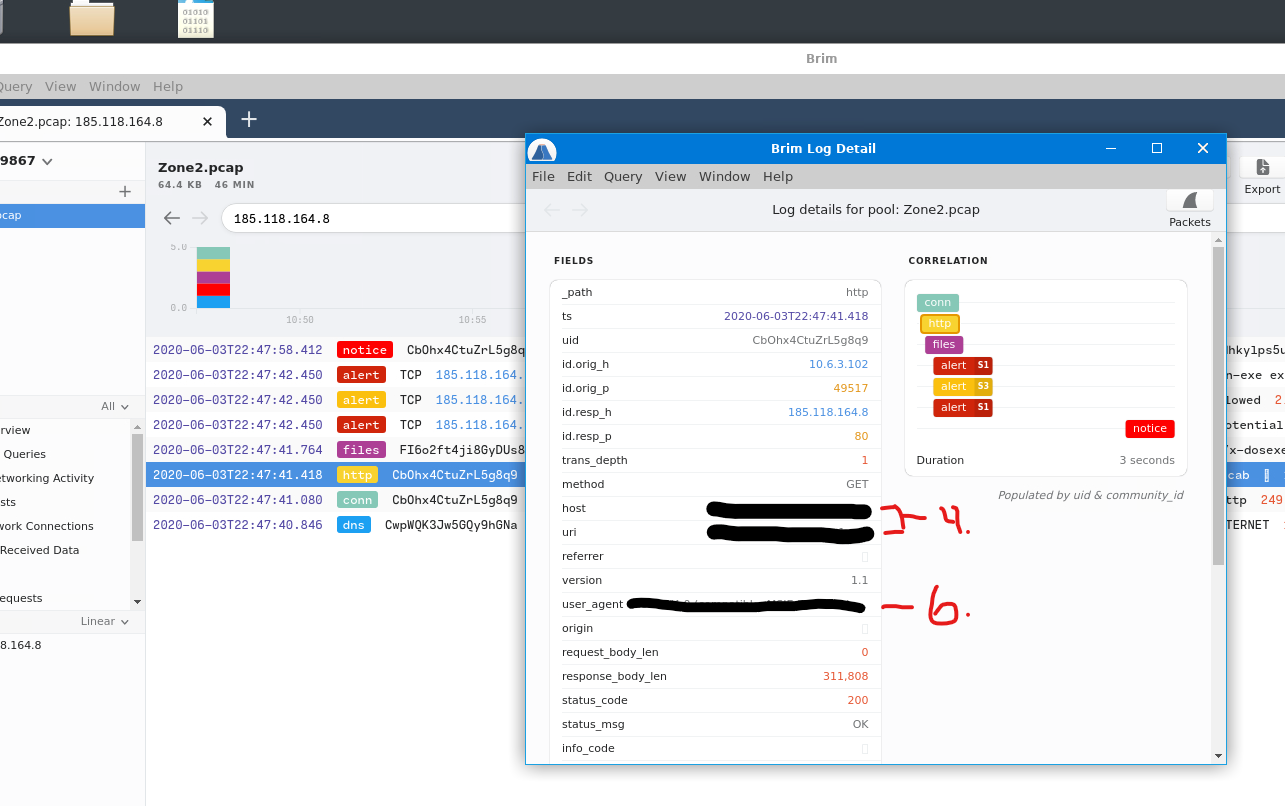
|
|
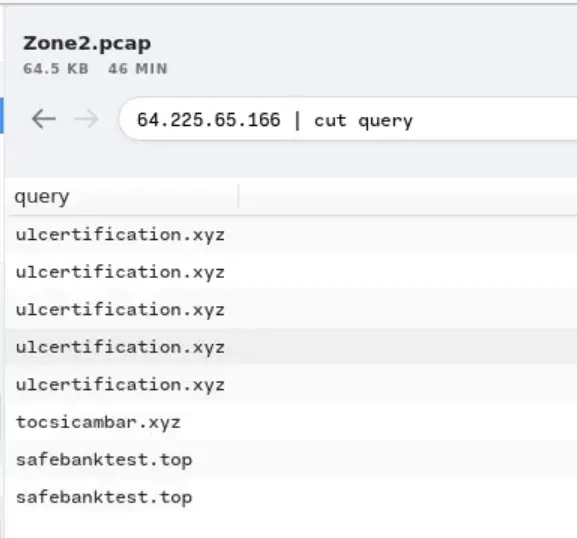
You'll find that this filters out the domains related to the IP address, you can then take domains and run a check against Virus Total for their reputation.
I want to apologize for the length of this write-up, this challenge was a long one to work on. But it was a good one! Thank you to ujohn for creating this challenge.
Happy Hacking everyone!